What's Data Sovereignty and Why Does It Matter
Data sovereignty means data is subject to the laws of the country where it's collected or stored. When a European company uses US cloud servers, which privacy laws apply? Can foreign governments access the data? These questions have real consequences.
The Compliance Reality
Regulations like GDPR, China's Cybersecurity Law, and India's Data Protection Act make data sovereignty mandatory. Companies face fines up to 4% of global revenue for violations. It's not optional anymore.
Why Standard Encryption Fails
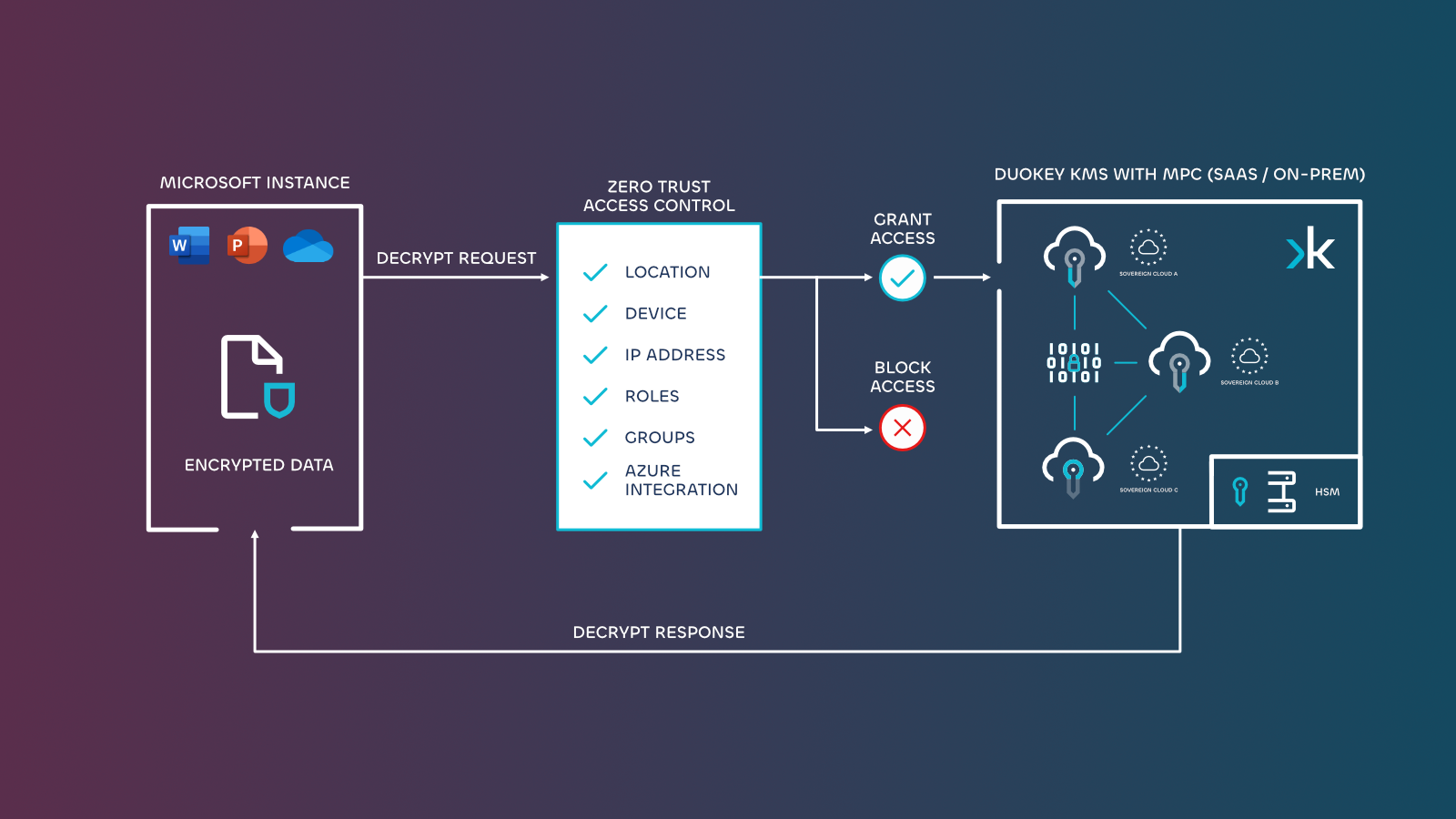
Traditional encryption creates a sovereignty problem: encrypt your data, give the keys to your cloud provider, and you've essentially handed over control. If that provider operates under different laws, your sovereignty guarantees disappear.
The Technical Solution
Modern cryptography like DuoKey solves this:
Multi-Party Computation (MPC) store encryption key without revealing it to any single party, including cloud providers. Your encryption key (and by extrapolation your data) stays under sovereign control regardless of where it's used.
Fully Homomorphic Encryption (FHE) enables computations and AI workflows on encrypted data without decryption. Providers can deliver services while never accessing plaintext.
Distributed Key Management eliminates single points of failure. When keys are split using MPC protocols, no single entity can unilaterally access your data.
Conclusion
Data sovereignty lets you use global infrastructure while meeting local regulations. The solution isn't avoiding international cloud services—it's using cryptography that maintains control regardless of server location.
Companies that treat sovereignty as an engineering problem, not just a legal constraint, will dominate their markets.