Watch DuoKey for DKE Demo
Experience true data security for Microsoft 365
Double Key Encryption (DKE)
Enhance Data Protection on Microsoft 365 with Double Key Encryption (DKE)
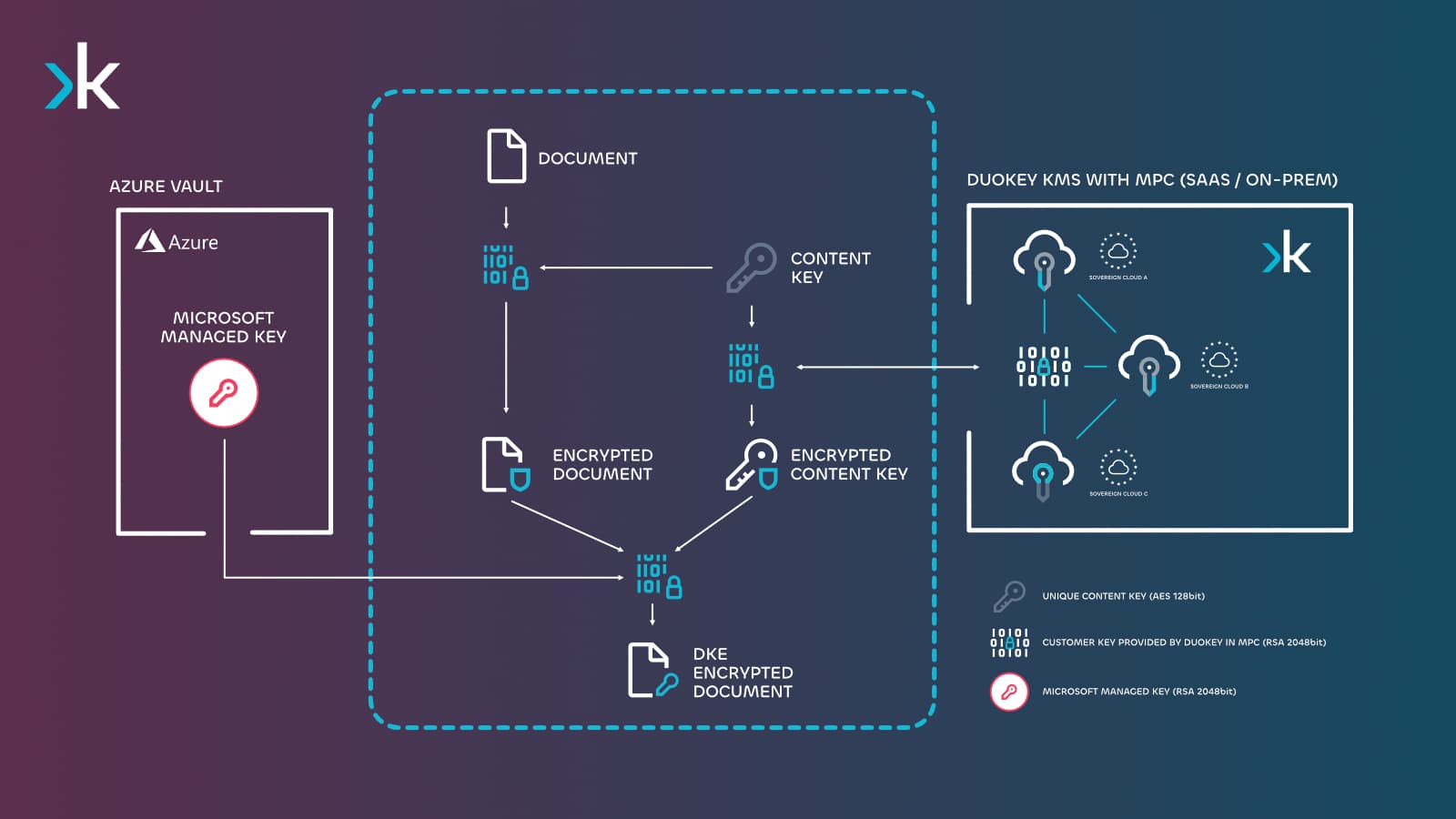
DuoKey for Double Encryption (DKE) provides distributed key management with MPC technology and zero-trust access controls, ensuring Microsoft has no access to your encryption keys while maintaining full data sovereignty and regulatory compliance.
Double Key Encryption (DKE) for Microsoft 365
Unparalleled Protection for Your Microsoft 365 Data with Double Key Encryption (DKE)
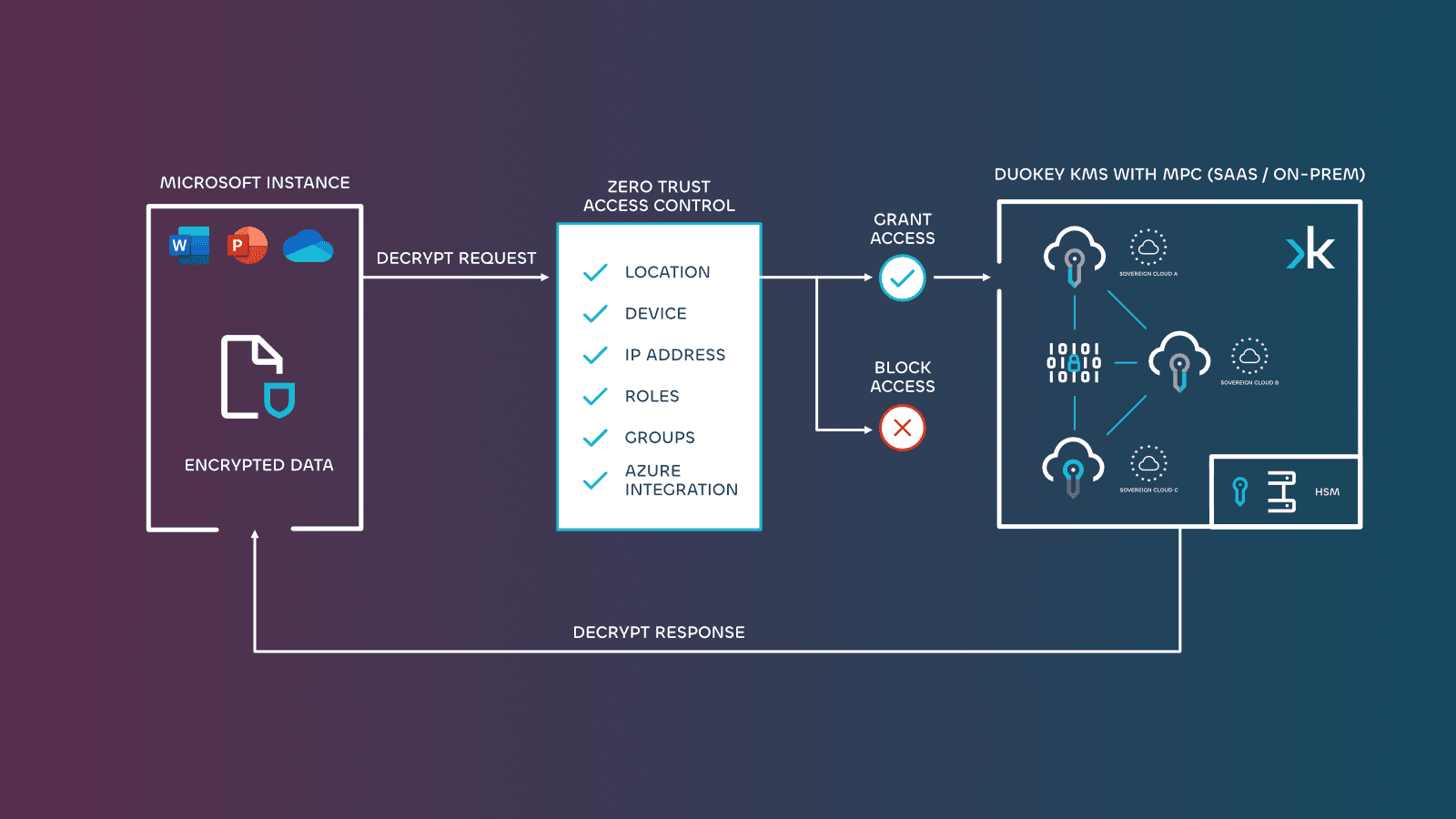
Advanced Zero Trust Access Controls
Enforce strict authorisation for every key access request through role-based permissions and multi-factor verification (eg. IP, Azure groups, location, user). Only verified users can access encryption keys, with continuous monitoring of all access attempts.
Learn more
MPC-Powered Distributed Key Management
Eliminate single points of failure with DuoKey secure Multi-Party Computation (MPC) key technology. Store your encryption into multiple shares distributed across different locations and systems, so that no single entity or compromised system can access complete keys.
What's MPC?Seamless Integration
Integrate DuoKey KMS with your current security infrastructure without requiring significant changes to established workflows or applications.

Advanced Zero Trust Access Controls
Enforce strict authorisation for every key access request through role-based permissions and multi-factor verification (eg. IP, Azure groups, location, user). Only verified users can access encryption keys, with continuous monitoring of all access attempts.
Learn moreFeedback
Our trusted partners
We appreciate DuoKey's cutting-edge approach to cloud security. Their double key encryption and advanced key management solutions not only enhance data protection but also ensure compliance. Utilizing advanced Multi Party Computation (MPC) protocols developed over decades by our team of acclaimed researchers, DuoKey delivers a superior level of cryptographic security, making it a reliable choice for safeguarding cloud applications and sensitive data.
Ahmet Tuncay - Former CEO, Sepior ApS
Blockdaemon Inc
DuoKey has revolutionized data security in our healthcare organization. Their encryption solutions provide robust protection for our sensitive health data, ensuring compliance and peace of mind.
CISO at Large Health NGO
Large Health NGO
Secure your data. Stay compliant.
Protecting cloud data, ensuring regulatory compliance and business continuity with DuoKey's DKE for Microsoft.

Compliance Assurance
Meets strict regulatory requirements like GDPR, HIPAA, and PCI DSS by implementing encryption standards that protect customer data and reduce legal liability risks

Operational Resilience
Maintains customer confidence and business operations by preventing costly data breaches, minimising downtime from security incidents, and preserving brand reputation

Advanced Data Protection
Encrypts sensitive data both at rest and in transit, ensuring unauthorised users cannot access sensitive information even if they breach cloud storage or intercept data transfers.
Take control of your encryption keys and protect sensitive data today!
Products
Other products in our arsenal
