Achieving Data Sovereignty in the AWS cloud
Protect Your Cloud Data with AWS XKS in 2025
Organisations across the globe are increasingly concerned about maintaining complete control over their AWS encryption keys and minimising the risk of unauthorised data exposure in the cloud. These concerns have become more pressing as businesses recognise that standard cloud security may not fully address their sovereignty requirements, particularly in light of legislation such as the CLOUD Act and FISA, and recent developments including the dismantling by the Trump administration of the Privacy and Civil Liberties Oversight Board.
For organisations using AWS and concerned about data privacy, this article examines protection options, with particular focus on AWS External Key Store (XKS) solutions that provide complete control, including DuoKey for AWS XKS which delivers data sovereignty through external key management.
Understanding Data Sovereignty Requirements for AWS
Achieving data sovereignty in AWS requires a comprehensive strategy that extends beyond standard cloud security measures. Organisations must implement a combination of technical safeguards, administrative policies, and contractual protections to create a robust security framework that ensures complete control over their data.
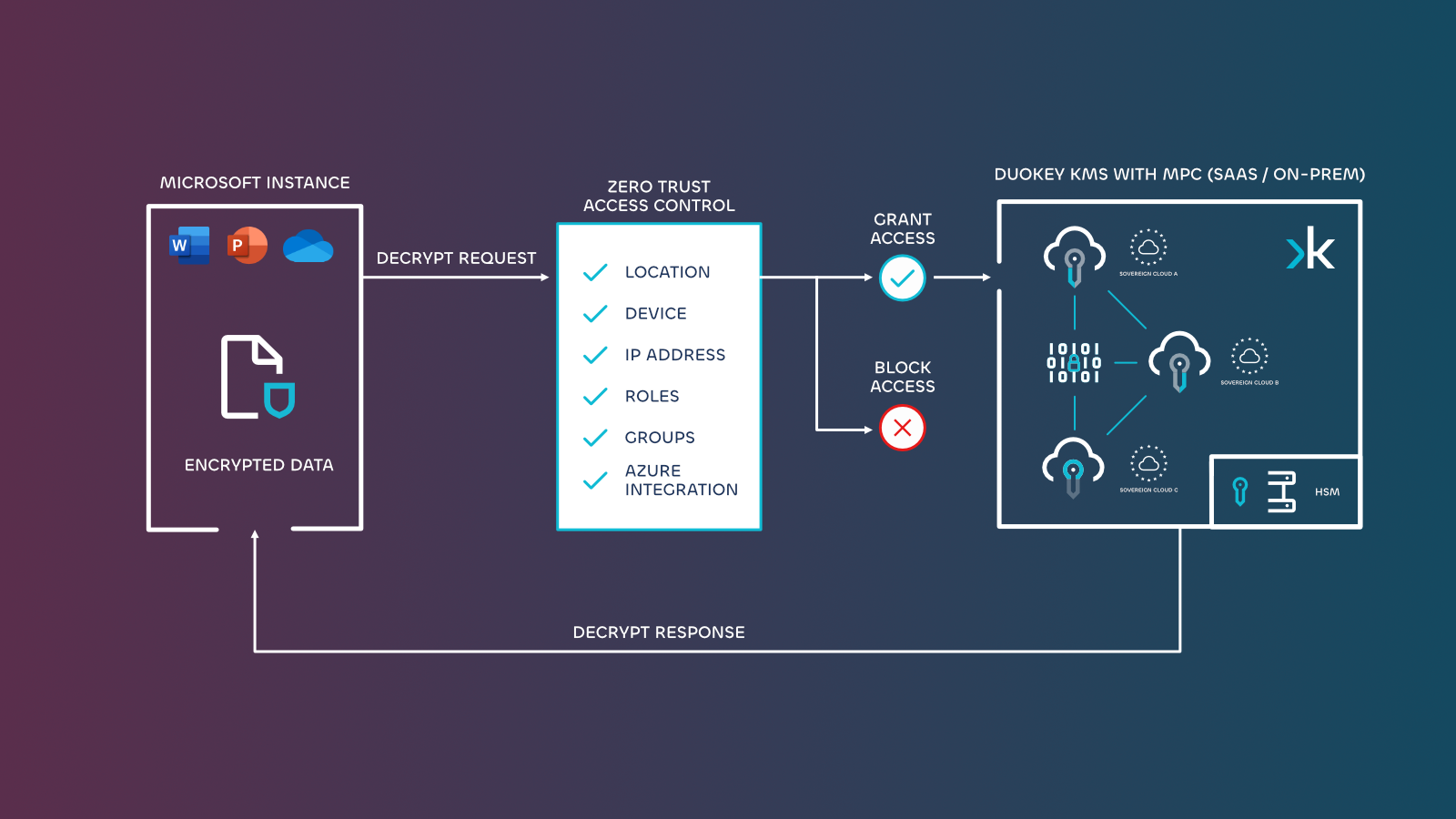
For true data sovereignty, organisations need absolute control over their encryption keys. This requires managing encryption keys independently of AWS, whilst still utilising AWS cloud capabilities. AWS External Key Store (XKS) and advanced solutions such as DuoKey address this requirement.
Let's examine each dimension, beginning with the critical technical measures that provide the strongest protection against unauthorised access.
Technical Measures to Protect AWS Data
Standard AWS Encryption Options
AWS includes several built-in encryption features as standard:
Amazon EBS encryption for storage volumes
AWS Key Management Service (KMS) for centralised key management
S3 server-side encryption for object storage
Transport Layer Security (TLS) for data in transit
AWS CloudHSM for hardware-based key storage
Whilst these provide baseline protection, they do not address concerns about potential data exposure linked to data breaches and government access requests served directly to AWS.
AWS Key Management Service (KMS) Standard Options
AWS KMS provides several key management approaches, each offering different levels of control:
AWS-Managed Keys AWS automatically creates and manages these keys. Whilst convenient, this approach provides limited control over encryption keys, as AWS maintains full access to the key material.
Customer-Managed Keys (CMK) These keys provide greater control over key policies, rotation, and access permissions. However, the underlying key material still resides within AWS infrastructure, meaning AWS could potentially access encrypted data if compelled by legal orders.
AWS CloudHSM This service provides dedicated hardware security modules (HSMs) within AWS infrastructure. Whilst offering stronger protection than standard KMS keys, the HSMs still operate within AWS data centres, limiting sovereignty.
AWS External Key Store (XKS): Complete Control Solution
AWS External Key Store (XKS) represents an effective technical response to surveillance concerns and delivers on the AWS Digital Sovereignty Pledge. As detailed in AWS's commitment to "Delivering on the AWS Digital Sovereignty Pledge: Control without compromise", External Key Stores support the AWS digital sovereignty pledge to give customers sovereign control over their data in AWS, including the ability to encrypt with key material that customers own and control outside of AWS. XKS provides superior protection through:
External Root of Trust: When configuring AWS KMS External Key Store (XKS), organisations replace the KMS key hierarchy with a new, external root of trust. Root keys are generated and stored inside an HSM that the organisation provides and operates
Complete Key Control: Encryption keys never leave the controlled environment
Double Encryption: DEKs protected by an XKS are doubly encrypted: once by KMS, and once by the external key manager
Access Revocation: Organisations can immediately revoke access to all encrypted data by disabling their external key store
Legal Protection: Even if AWS receives a valid legal order, data remains protected by keys they cannot access

How AWS XKS Operates
AWS KMS never interacts directly with external key managers, and cannot create, view, manage, or delete keys. Instead, AWS KMS interacts only with external key store proxy (XKS proxy) software that organisations provide.
The XKS architecture ensures:
External Key Management: All encryption keys are generated and stored in external HSM or key management systems
Proxy-Mediated Access: AWS KMS communicates only through XKS proxy, never directly with keys
Hold Your Own Keys (HYOK): Cryptographic key material never leaves the external key manager
Transparent Integration: Works with over 100 AWS services that support KMS
DuoKey for AWS XKS: Data Sovereignty Solution
DuoKey has developed XKS implementations that provide comprehensive data sovereignty features.
DuoKey for AWS XKS enables organisations to:
Maintain data sovereignty: Retain complete control over encryption keys outside AWS infrastructure
Meet regulatory requirements: Comply with data protection regulations including GDPR, CCPA, and sector-specific mandates
Control encryption keys: Generate, store, and manage keys using organisational infrastructure or trusted third-party HSMs
Protect sensitive data: Ensure that neither AWS nor any other party can access encrypted data without explicit authorisation
DuoKey for AWS XKS
DuoKey for AWS XKS include the following features.
Hardware Security Module (HSM) Integration - DuoKey for AWS XKS works with both hardware security modules (HSM) and secure multi-party computation (MPC) deployments on AWS Nitro Systems, providing deployment flexibility whilst maintaining security standards.
Distributed Key Management Uses secure Multi-Party Computation for key distribution to mitigate single point of compromise, ensuring keys remain protected even if individual components are compromised
Deployment Options Available for on-premises, SaaS, or hybrid deployments, compatible with many existing HSM models, allowing organisations to select deployment models that fit their requirements.
Centralised Management Provides centralised encryption key management with full lifecycle management and comprehensive audit trails, supporting compliance and operational oversight.
Benefits of AWS XKS with DuoKey
Enhanced Security
Cryptographic keys reside outside of the AWS KMS cloud, ensuring that only authorised parties can decrypt protected content, mitigating unauthorised access risks.
Regulatory Compliance
Organisations can control data encryption keys and store them on premises. This prevents AWS access to keys and data, which may be required under regulations such as the CLOUD Act.
Operational Control
Organisations can control key access and use whilst maintaining complete provenance of root keys, ensuring full visibility and control over key usage.
Business Continuity
Access revocation functionality allows immediate termination of data access, providing control in emergency situations or compliance scenarios.
Simplified Multi-Cloud Strategy
Enables organisations to centralise key management strategies across AWS and SaaS solutions by providing a central location to manage access policies and audit key usage.
Contractual and Administrative Safeguards
Whilst technical measures such as DuoKey for AWS XKS provide strong protection, a complete data sovereignty strategy should also include contractual and administrative safeguards.
Contractual Measures
Review AWS Data Processing Addendums and understand organisational rights
Evaluate AWS region selection and data residency options
Consider AWS Multi-Region configurations for data sovereignty
Implement Data Processing Agreements (DPAs) with third-party providers
Administrative Controls
Implement comprehensive data classification policies
Train staff on secure cloud collaboration practices
Establish incident response procedures for potential data access requests
Develop key management policies and procedures
Create audit trails and monitoring procedures
Industry Recognition and Ecosystem
As outlined in the AWS Digital Sovereignty Pledge blog post, AWS has collaborated with external HSM, key management, and integration service providers. Thales, Entrust, Fortanix, DuoKey, and HashiCorp have launched XKS implementations, with Salesforce, Atos, and T-Systems building integrated service offerings around XKS, demonstrating the maturity and industry adoption of XKS solutions.
The open source XKS specification provides flexibility and ensures that organisations can choose from multiple vendors and implementation approaches based on their specific requirements.
Implementing AWS Data Sovereignty
AWS External Key Store with DuoKey provides a practical solution for organisations seeking to enhance data sovereignty in AWS whilst addressing data exposure concerns and regulatory requirements.
By implementing XKS through providers such as DuoKey, organisations can maintain control over their data, ensuring that neither AWS nor other parties can access encrypted information without explicit authorisation.
Summary
Standard AWS encryption does not provide complete data sovereignty
AWS-managed keys present potential exposure risks
External Key Store (XKS) prevents data exposure through external key management
DuoKey provides an XKS solution featuring secure Multi-Party Computation and access control for data sovereignty
With XKS and DuoKey, organisations maintain complete control over data access
XKS provides access revocation capability for immediate data access termination
The solution integrates with over 100 AWS services whilst maintaining external key control
Sources
AWS Digital Sovereignty Pledge: Control without compromise: https://aws.amazon.com/blogs/security/aws-digital-sovereignty-pledge-control-without-compromise/
Announcing AWS KMS External Key Store (XKS): https://aws.amazon.com/blogs/aws/announcing-aws-kms-external-key-store-xks/
Data Encryption: https://docs.aws.amazon.com/whitepapers/latest/introduction-aws-security/data-encryption.html
Digital Sovereignty with DuoKey