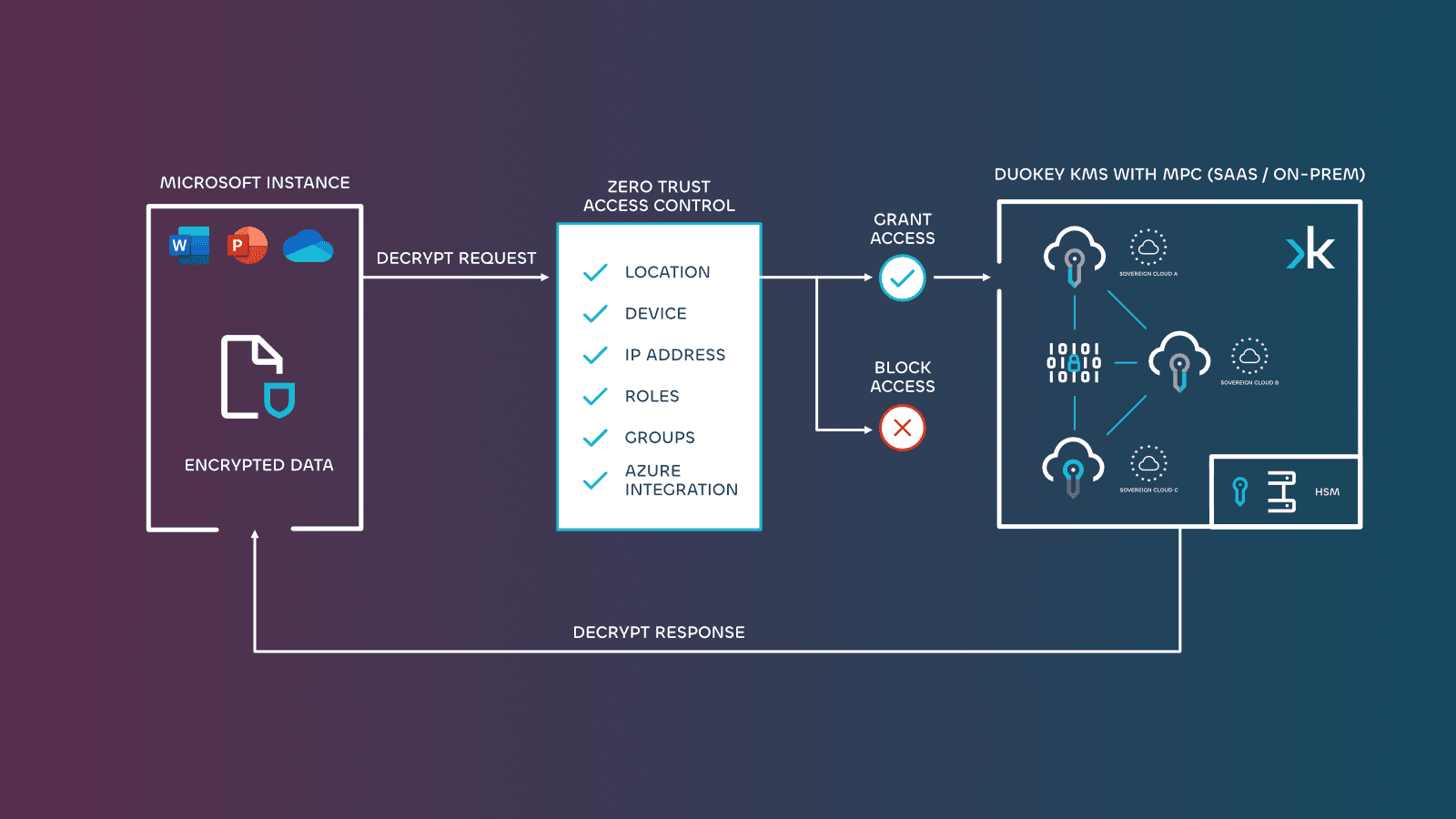
DuoKey Zero-Trust Access Control for Microsoft 365
DuoKey for Double Key Encryption (DKE) includes zero-trust access controls that integrate with Azure AD, providing organisations with the ability to control encryption key access through conditional verification outside of Microsoft 365
While Microsoft 365 employs robust encryption to protect data, it lacks granular controls over who can access the encryption keys themselves, creating potential security gaps.
When an authorised user has access to keys, that access is generally binary - they either have it or they don't, regardless of other risk factors like location or device security.
Zero-trust for Key Access in Microsoft 365
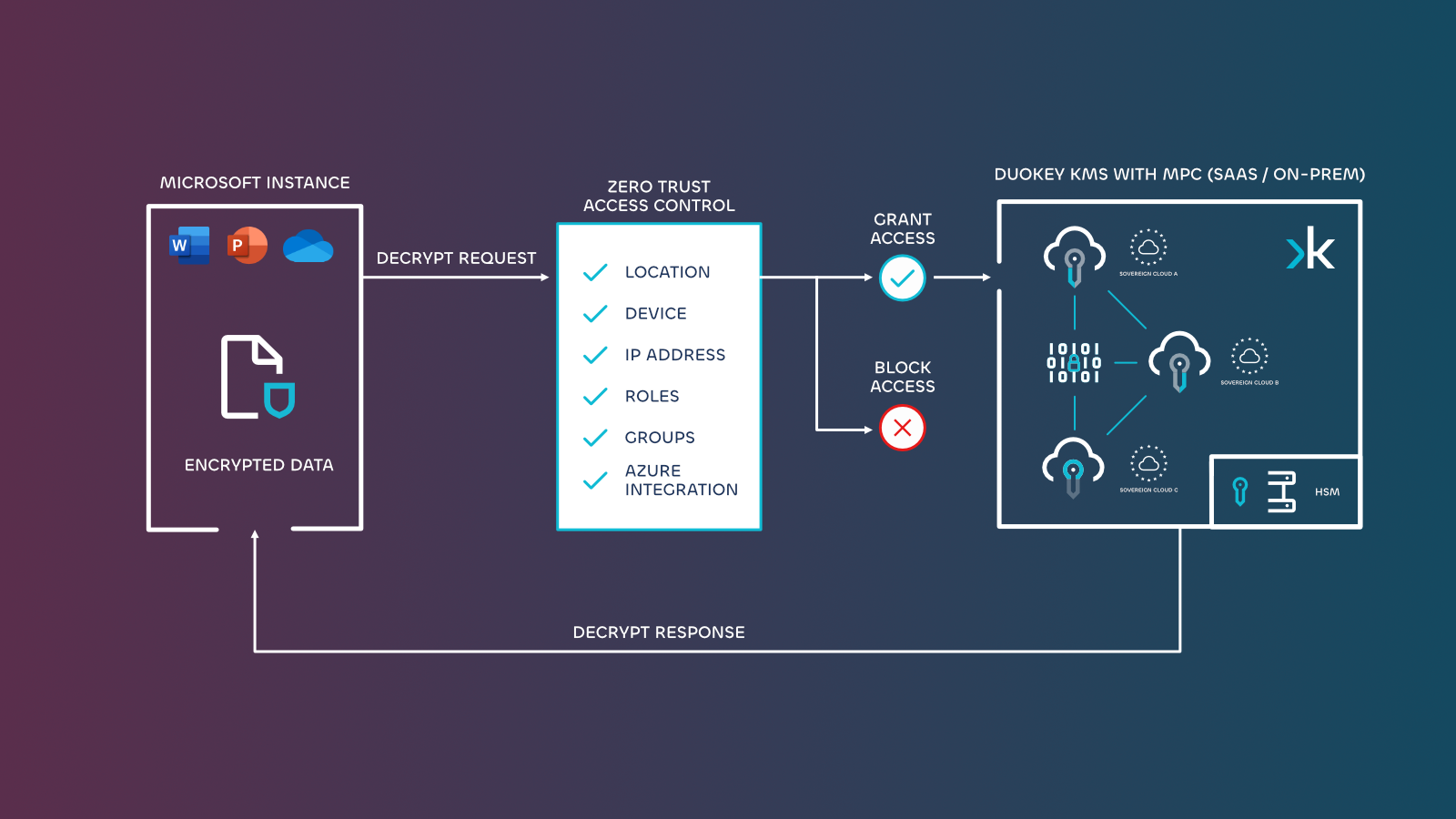
DuoKey zero-trust access controls
DuoKey addresses this gap by providing zero-trust principles specifically for encryption key management in its data encryption module for Microsoft 365 url(duokey for microsoft). The system integrates with Azure AD to evaluate multiple factors before granting access outside of Microsoft, including:
Geographic location: Restrict key access to specific countries or regions
Device status: Require managed or compliant devices
Network identification: Limit access to known IP ranges
User roles: Apply different policies based on Azure AD roles
Group membership: Control access based on security group assignment
This approach ensures that even authorised users must meet additional security criteria before accessing encryption keys.
Schedule a demo to see how these zero-trust controls integrate seamlessly with your Microsoft 365 environment and enables you to achieve data sovereignty in Microsoft 365.

DuoKey for Microsoft 365 integrates these industry-first zero-trust controls into its advanced key management system (KMS). The solution leverages Double Key Encryption (DKE) and distributed key management, with flexible deployment options including SaaS, on-premise, or hybrid models.